(ISC)² Security Congress 2022 - day one
Congress got off to a great start and included a heart-warming (and I'll be honest tear inducing) story from one of the speakers.
Welcome to the first blog post of my Security Congress 2022 series, where I'll be blogging about my experiences at (ISC)² Security Congress conference. If you're interested in my posts from Congress 2021 they're here.
This year's conference is being hosted in Las Vegas, and given the cost in flights would be huge, and I'd probably not cope with that huge number of people, I opted to attend the conference from home. By the looks of it, not every session is available online (e.g., some of the vendor talks like "Solutions Theatre" presentations) but the conference still looks to have a good selection of talks.
Most of the time I've opted not to display the speaker's full name or company unless I know that information is already public.
My schedule
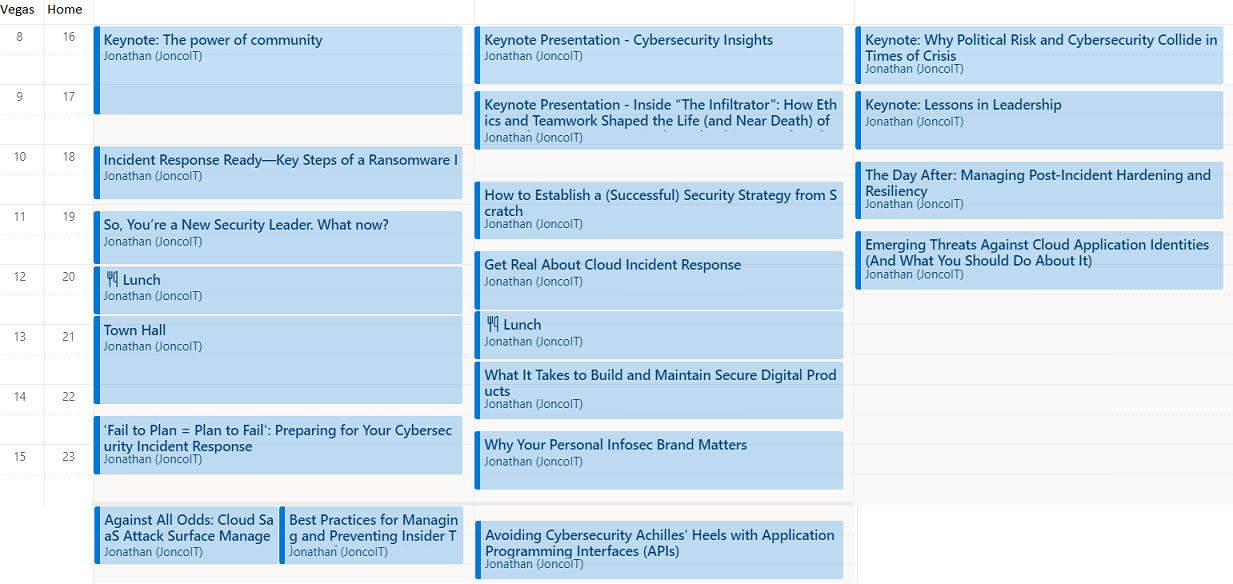
With Las Vegas being eight hours behind British Summer Time (BST), my daily sessions take me across two days hence the stitched together screenshot above (i.e., Monday talks in Vegas actually finish about an hour into my Tuesday). Starting at 16:00 and finishing around 01:00 UK time, I've got seventeen sessions booked to attend live. After the conference finishes, I'll still be able to access the other sessions that I couldn't attend (time collisions).
The keen eyed amongst you will notice that Monday night I've got two sessions at the same time. That's to remind me that I want to view the second session (Best Practices for Managing & Preventing Insider Threats from Interviewing Experts) on "catch up" tomorrow, whilst attending Against All Odds: Cloud SaaS Attack Surface Management today.
This year's setup
As my side project consultancy now has a Windows laptop, I decided I'd use that to attend Congress, rather than my Linux laptop as I did last year. There was only one issue last year, and that was the professional networking website didn't like my Linux browser. I'm not expecting any problems with any of the conference now I'm running from Windows. For audio I'm using my Anker Soundcore Q30 active noise cancelling headphones (I should review those at some point...).
I'm taking notes again (otherwise these blog posts would be a challenge!) typing directly into OneNote.
Conference kick off: The Power of Community
Online, we were let into the first session about fifteen minutes early and left to chat with each other while various music played. Not your stereotypical "elevator music" but some reasonably popular tunes from a number of decades.
Unlike last year, where the whole event was online, this year was a hybrid event, and it was interesting to see presenters on a stage rather than in their homes. Clar Rosso, the CEO, opened the session explaining how there's 4.7 million cyber security professionals globally, an increase of 11% in a year but there's still a deficit of 3.4 million people. Further, two out of three professionals say they don't have enough staff, so deem their organisation to be at risk. Clar told us how part of the solution to this is to break down barriers to entry, and to then help people stay in the cyber security field - it seemed Clar was echoing her diversity and inclusion comments from Congress 2021 (and she's not wrong). We also heard how (ISC)² was deepening its links with national agencies, including the UK's NCSC.
Clar handed the floor to four speakers who then shared how their organisations were working on or with the community. I have a lot of notes from this, but a summary:
- The former attitude of being stronger than the next organisation, so attackers go after them instead, is outdated. We're stronger together through collective defence (Ann from a US department)
- Bryson (CEO of a security company) shared, while wearing a black unicorn hoodie, "Your assets only work in a way you designed them to work" - design your environment to work in a secure way - segregation is important. He also shared how AI needs good training data, and how we have to monitor it to make sure it's still doing what we expect it to do
- Mari from a women's IT society highlighted how the community working together to mentor others and support people really helps people with their careers
- Andrew had gone into Ukraine to help get his colleagues out when the war broke out. Other than caring for people hugely, he shared some advice to apply to our own cyber security strategies:
Maintain an awareness of business risk and of current events
Respond early wherever possible
Communicate early and often
Understand the psychology of crisis (people react in different ways)
Clar Rosso awarded Andrew the CEO's award, in recognition of his commitment to people.
(ISC)²'s own bloggers got a post published not long after the opening session was finished - read their summary here.
Incident Response Ready - Key Steps of a Ransomware Incident Response Plan
In this session, Joe took us through a real ransomware attack, and the learning points. Joe started by highlighting to us that you'll most likely find out about the incident from a third party - either the attacker, law enforcement, or maybe a customer. Once you start your own response you may also find data from other parties, so the community spirit of "hi, I found this in relation to you, do you have additional information / can I provide you some?" could be beneficial. Obviously there's a need to be careful with the data that's shared.
During incident response you may find details about breaches or crimes unrelated to your current case. For example, having looked at logs going back five years it was discovered an employee had installed a crypto miner two years previously. While you probably cannot dedicate resources to handling that discovery immediately, it does need looking into later.
Part of the response needs to include determining how the attacker got in and mitigating that for the future. Once they were in, how did they disable further security protections and then move around the network? Don't forget the "lessons learned" phase of the incident response process!
Something that Joe mentioned that I've seen elsewhere before (and noted that I really should do), is the benefit of having an incident response "go bag" containing equipment (network cable, power packs, USB sticks...), food (you could be in for a long night!) and a copy of your processes (playbooks etc.) as they may have been encrypted as part of the attack. In one of the case studies from the talk, the victim organisation was having to order parts, including memory sticks, for next day delivery - not a good position to be in.
Joe ended by taking us through a demo that reproduced the attack (albeit in a lab and thus anonymised). Once the attacker was on a workstation there had been a text file on the desktop called Important Stuff which had contained IP addresses, usernames and passwords. This allowed the attacker to pivot to another system. My advice would be to deploy a company-wide password management solution so colleagues can store such information securely.
Another key contributor to the success of the attack was the fact the compromised user had local administrator privileges. While you may argue "they're only local, not network", it's not hard for an attacker to leverage their local privilege to gain network administrator privileges. Joe's advice was to have robust monitoring and reporting in place in the event users have to have local administrator rights.
So, You’re a New Security Leader. What now?
I couldn't find this session, despite it having been there last week. Speaking to support I found, sadly, this session got cancelled, prompting a quick rethink. Hopefully the speaker is OK.
The first replacement session that I picked I couldn't get on with, so I changed to...
Self-Protecting Data: An Artificial Intelligence Use Case
Obviously, I missed the beginning of this session, so felt I was missing some context. The basic challenge seemed to be the need to be able to have data protect itself, and report back in the event of tampering. This was particularly true for defense data, and the speaker was from the US Air Force. Research by some students used Python to create a file wrapper that would encrypt a file, and then only allow decryption on presentation of the correct key and optionally while inside a specific geographical area. The file wrapper could delete the file after a period of time and also self-destruct the file on a failure of decryption.
Goals for the technology included the need for the solution to be file type agnostic, plus the ability to not need to "phone home".
Town Hall
For me, probably the most useful part of the town hall was chatting with others in the text chat sidebar. That's not to say I wasn't paying attention, there's definitely some interesting changes coming.
There was talk earlier of removing barriers to entry to the profession, and some new certificates (not certifications) aim to help with that. Once you've got the certificate you'd still have to sit a full examination to get a certification (for example the CISSP (read my post about my CISSP experience). From the standpoint of a certification holder, it's good to hear that changes to the syllabus, and the introduction of the certificates, will not require a recertification - just keep up with your continual professional education (CPE) and annual maintenance fee.
Also of note is the certified in cybersecurity certification, which (ISC)² is giving away free, the training and exam, to one million people. This certification can be achieved by those with no experience and can be useful for hiring managers, as they can focus on non-technical aspects of the candidate. Individuals that are looking to see if cybersecurity can use the training and certification to see if this industry is really for them. More information here.
Lori from the board asked us all to encourage people that are looking to get into the industry. Even if that's not formal mentoring. Mentoring can also be incredibly rewarding, says our CISO, Jon.
There's been awards given out at a few of the main hall presentations, which is cool to see, and three more were issued at the end of this session. More details on the awards here.
'Fail to Plan = Plan to Fail' - Preparing For Your Cybersecurity Incident Response
Once in this session, but before the actual presentation, we were taught some physiotherapy exercises that focussed on the head, neck, shoulders and arms. I was concerned the unexpected physio would cause talks to overrun, but then noticed that it was all pre-session, so all good there 😊. It was good for this to be laid on, as IT is often a static job spent sat in chairs.
I'll be honest, I found this session a massive disappointment. Part way through the session I asked in the chat if anyone else was having problems aligning the content to the session title and description in the conference planner, and reassuringly I was not the only one. This question was put to the speaker during the Q&A, and they explained that when they realised it was going to be a talk about how to be prepared for a cyber security incident, that there was so much content out there already. There was no right answer and that if we all focus on the playbooks for response that doesn't mean our organisations would respond well to an incident. Instead, they decided to "flip the script" and made this a talk that was technology focused on hybrid cloud, artificial intelligence and blockchain.
I don't know what "flip the script" means - possibly "to advertise something and do the opposite" - but I was not alone in feeling that had the description and title matched the content that I would have picked a different talk.
Blockchain got mentioned a lot as a way to help with supply chain security, although I wasn't able to fully grasp why (partly due to being confused by the title/content mismatch). It was also suggested that a fully deployed AI solution could allow organisations to realise $3.05 million in savings. While I agree that taking menial work away from humans, and getting computers to do it, is worthwhile, I struggled to correlate the suggested saving with any organisation I've ever worked for. The statistics come from an IBM report looking at organisations in seventeen countries, so perhaps they are much bigger organisations than I've been in. Similarly, the statistic that the average cost of a data breach was $4.35 million seemed high based on organisations I've worked for (unless it was "worst case").
All in all, not a useful session for me.
Against All Odds: Cloud SaaS Attack Surface Management
Sadly another session that I didn't particularly benefit from, as it didn't seem to unpack the threat modelling aspect. Probably the most useful takeaway for me was a reinforcement that a "lift and shift" from on-prem to the cloud doesn't make an application "cloud native". It's necessary to refactor the code to take advantage of cloud native technologies including containers and microservices.
It's also important to ensure third parties that you work with, particularly as authentication providers, meet your organisation's security policies at a minimum. Otherwise the third party becomes a weak link in the chain.
The talk description said we'd be diving deep into threat modelling attack libraries and applying them to web applications. We didn't seem to do that, but apparently the handout (not yet available) has further guidance, so it'll be good to refer to that once it's available.
End of day one
Overall, a good start to the conference, but with some disappointing sessions towards the end. I do accept that sessions don't always appeal to all people, and as I can watch other sessions on catch up it's not a huge problem.
Looking forward to day two!
Banner image: Screenshot of the virtual conference venue landing page.

