What is a Next Generation firewall?
A look at Next Generation firewalls and the extra services they often provide.

In a previous post I discussed what a basic firewall is, and how it works. Firewalls don't stop at the basic level though, with modern firewalls doing much more than just filtering[1] packets based on a set of source/destination/port based rules.
Historically there tended to be one device per job, so if you wanted a web filter, intrusion detection system (IDS), intrusion prevention system (IPS) and firewall you'd need four boxes. Being "next gen", the firewall has converged many of these tasks into a single device. That convergence still has pros and cons, but now hardware is more powerful a single device is much more feasible - after all these are just computers really.
The concepts I discussed in my last post on firewalls still hold true for next gen devices. Let's dive in!
Application aware: a bouncer checking photo ID
To continue the bouncer analogy from the previous post, a application aware next-gen firewall will not only ask your name (the source/destination/port component) but will also check you match a registered photo ID. We can liken the photo ID check to the firewall examining the type of traffic and matching that to a known signature.
For example, many years ago I configured a server at home to listen for SSH (Secure Shell) on TCP port 443 (typically HTTPS). Usually SSH would use TCP port 22 but, knowing this wasn't likely to be permitted through the firewall between me and my server, I switched to 443 as that would be allowed.
Had the firewall between my client and my server been application aware, my traffic would have been blocked because SSH traffic has a different signature to HTTPS. Technically, with encrypted traffic, that's only true so long as the firewall is intercepting and inspecting the traffic, more on that later.
Proxying traffic
In order to perform extra functions like web filtering, the next gen firewall will proxy traffic. A proxy makes the connection to a remote system on your behalf, terminating your connection, in much the same way someone can proxy vote for you (voting on your behalf at an election). This is well explained in the graphic below, drawn by H2g2bob.
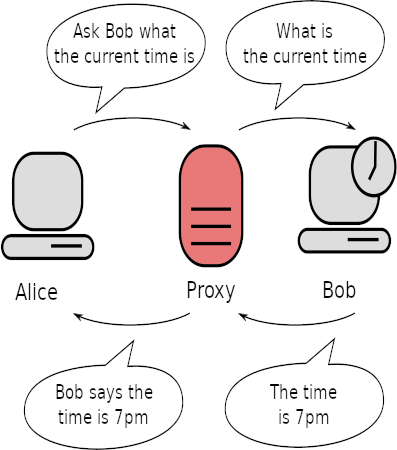
In the case of a next gen firewall acting as a web proxy, the firewall would receive a request for a website from the client. The firewall then requests the page from the web server and provides the answer back to the client. Because the firewall is making the request for you, it can choose not to make the request. For example, if the firewall has been configured not to allow access to www.example.org the firewall's proxy can simply return a page that says "this site is banned". Often this control is done based on category lists (e.g. blocking sites about gambling but allowing charity sites) rather than individual sites.
Proxying can take place for more than just website traffic - I've seen SMTP (Simple Mail Transfer Protocol - email) and SSH (Secure Shell) proxies amongst others. Unless encrypted traffic inspection is enabled the proxy wouldn't be able to inspect the traffic though.
When proxying we can take a number of actions including scanning with anti-virus and blocking certain file types from being downloaded.
Encrypted traffic inspection

As mentioned earlier, actions can only be taken on encrypted traffic if it's being intercepted and inspected. To do that it's necessary to perform a man in the middle attack, albeit an authorised attack. The firewall first decrypts the traffic, then reads its data before encrypting it again:
- Sender transmits the message
- Firewall inspects the message, decrypting it as necessary
- Message is re-encrypted with the firewall's certificate and passed to the recipient
Because the firewall has decrypted the traffic it's able to make decisions based on the information inside. For example, without this inspection it would not be possible to filter web pages served over HTTPS. We can also now scan the once-encrypted data with anti-virus to check we're not being served known malware as distributing malware over HTTPS is a trick sometimes used by attackers.
This type of inspection is sometimes called deep inspection but in order for it to work the client devices (the recipient in this scenario) needs to trust the firewall's certificate. Certificate trust is a blog post in itself but, in summary, your computer already trusts certificates from certain Certification Authorities including Let's Encrypt, Microsoft, Google et al. When doing deep inspection we install the firewall's certificate into our client's trusted certificate store in order to avoid getting errors when browsing to secured pages.
Another type of inspection involves just checking that the certificate is from a trusted source. With the firewall only validating the certificate it's not necessary to distribute a certificate to our clients but we also can't inspect the traffic.
Web Application Firewall functionality
Web Application Firewalls (WAF) inspect requests sent to a web site and determine if the request is legitimate ("please give me this page") or an attack like an attempt at SQL injection. If an attack is found the WAF will either try to clean it up or drop the traffic. Optionally the WAF can instruct the firewall to block the malicious actor.
Signatures are used by the WAF in much the same way anti-virus does. Request traffic is compared to the signatures in order to determine the traffic type. WAF definitions tend to be a paid for subscription in order to stay updated.
False positives are possible, as with any technology, so it's important to test the WAF in alert only mode before enabling full blocking.
Virtual Private Networking
A Virtual Private Network (VPN) is a secure connection between your client and, for example, your office. VPNs are also becoming popular among the general public for protecting their traffic and giving greater privacy.
Some next generation firewalls can terminate VPN connections, meaning the firewall is responsible for the VPN connection. The firewall will authenticate the user (or check the user's credentials against an external database such as Active Directory) and then set up the secure tunnel. By handling the VPN tunnels on the firewall itself it's possible to restrict where VPN clients can go by adding firewall rules.
Conclusion
A next generation firewall is really just a convergance device to perform multiple security functions at once. This is made possible by the invention of more powerful hardware, saving the need for additional devices.
You can treat a next generation firewall like a standard packet filtering device, and I know several companies that have never enabled the extra functionality, but I'd certainly recommend considering making use of the extra features. There are many more features than I've covered here, this is just an overview.
Banner image, firewall, from Openclipart.org (before it disappeared).
[1] Filtering - to make a decision as to whether the traffic should be allowed based on firewall rules
[2] From https://commons.wikimedia.org/wiki/File:Proxy_concept_en.svg
Images in diagrams from OpenClipart.org before it disappeared unless otherwise credited.

